2016/09 New Microsoft 70-411: Administering Windows Server 2012 R2 Exam Questions Released Today!
Free Instant Download 70-411 Exam Dumps (PDF & VCE) 445Q&As from Braindump2go.com Today!
100% Real Exam Questions! 100% Exam Pass Guaranteed!
1.|2016/09 Latest 70-411 Exam Dumps (PDF & VCE) 445Q&As Download:
http://www.braindump2go.com/70-411.html
2.|2016/09 Latest 70-411 Exam Questions & Answers:
https://drive.google.com/folderview?id=0B75b5xYLjSSNfnNyWDFTYllvTTkteG0waVJYSFdoaDVWZTBSamh6Q0xiaUJmNEk5cUJSbFU&usp=sharing
QUESTION 11
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Network Policy Server server role installed.
You need to allow connections that use 802.1x.
What should you create?
A. A network policy that uses Microsoft Protected EAP (PEAP) authentication
B. A network policy that uses EAP-MSCHAP v2 authentication
C. A connection request policy that uses EAP (PEAP) authentication
D. A connection request policy that uses MS-CHAP v2 authentication
Answer: B
Explanation:
802.1X – uses EAP, EAP-TLS, EAP-MS-CHAP v2, and PEAP authentication methods:
EAP (Extensible Authentication Protocol) uses an arbitrary authentication method, such as certificates, smart cards, or credentials. EAP-TLS (EAP-Transport Layer Security) is an EAP type that is used in certificate- based security environments, and it provides the strongest authentication and key determination method.
EAP-MS-CHAP v2 (EAP-Microsoft Challenge Handshake Authentication Protocol version 2) is a mutual authentication method that supports password-based user or computer authentication.
PEAP (Protected EAP) is an authentication method that uses TLS to enhance the security of other EAP authentication protocols.
Connection request policies are sets of conditions and settings that allow network administrators to designate which Remote Authentication Dial-In User Service (RADIUS) servers perform the authentication and authorization of connection requests that the server running Network Policy Server (NPS) receives from RADIUS clients. Connection request policies can be configured to designate which RADIUS servers are used for RADIUS accounting.
With connection request policies, you can use NPS as a RADIUS server or as a RADIUS proxy, based on factors such as the following:
The time of day and day of the week
The realm name in the connection request
The type of connection being requested
The IP address of the RADIUS client
QUESTION 12
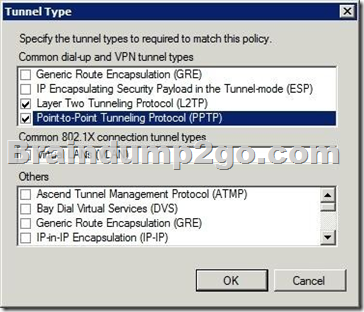
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Remote Access server role installed. On Server1, you create a network policy named PPTP_Policy.
You need to configure PPTP_Policy to apply only to VPN connections that use the PPTP protocol.
What should you configure in PPTP_Policy?
A. The Service Type
B. The Tunnel Type
C. The Framed Protocol
D. The NAS Port Type
Answer: B
Explanation:
A. Restricts the policy to only clients specifying a certain type of service, such as Telnet or Point to Point Protocol connections.
B. Restricts the policy to only clients that create a specific type of tunnel, such as PPTP or L2TP.
C. Restricts the policy to clients that specify a certain framing protocol for incoming packets, such as PPP or SLIP.
D. Allows you to specify the type of media used by the client computer to connect to the network. http://technet.microsoft.com/en-us/library/cc731220(v=ws.10).aspx
QUESTION 13
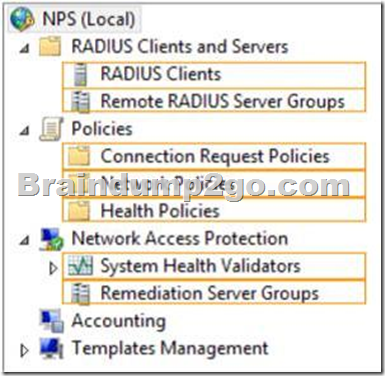
Your network contains a RADIUS server named Server1.
You install a new server named Server2 that runs Windows Server 2012 R2 and has Network Policy Server (NPS) installed.
You need to ensure that all accounting requests for Server2 are forwarded to Server1.
On Server2, you configure a Connection Request Policy.
What else should you configure on Server2?
To answer, select the appropriate node in the answer area.
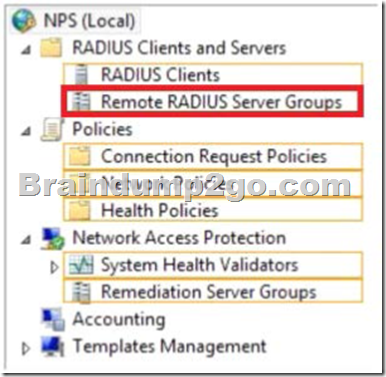
Answer:
Explanation:
When you configure Network Policy Server (NPS) as a Remote Authentication Dial-In User Service (RADIUS) proxy, you use NPS to forward connection requests to RADIUS servers that are capable of processing the connection requests because they can perform authentication and authorization in the domain where the user or computer account is located. For example, if you want to forward connection requests to one or more RADIUS servers in untrusted domains, you can configure NPS as a RADIUS proxy to forward the requests to the remote RADIUS servers in the untrusted domain. To configure NPS as a RADIUS proxy, you must create a connection request policy that contains all of the information required for NPS to evaluate which messages to forward and where to send the messages.
When you configure a remote RADIUS server group in NPS and you configure a connection request policy with the group, you are designating the location where NPS is to forward connection requests.
http://technet.microsoft.com/en-us/library/cc754518.aspx
QUESTION 14
Your network contains two Active Directory forests named contoso.com and adatum.com. The contoso.com forest contains a server named server1.contoso.com. The adatum.com forest contains a server named server2.adatum.com. Both servers have the Network Policy Server role service installed. The network contains a server named Server3. Server3 is located in the perimeter network and has the Network Policy Server role service installed.
You plan to configure Server3 as an authentication provider for several VPN servers.
You need to ensure that RADIUS requests received by Server3 for a specific VPN server are always forwarded to server1.contoso.com.
Which two should you configure on Server3? (Each correct answer presents part of the solution. Choose two.)
A. Network policies
B. Remote RADIUS server groups
C. Connection authorization policies
D. Remediation server groups
E. Connection request policies
Answer: BE
Explanation:
When you configure Network Policy Server (NPS) as a Remote Authentication Dial-In User Service (RADIUS) proxy, you use NPS to forward connection requests to RADIUS servers that are capable of processing the connection requests because they can perform authentication and authorization in the domain where the user or computer account is located. For example, if you want to forward connection requests to one or more RADIUS servers in untrusted domains, you can configure NPS as a RADIUS proxy to forward the requests to the remote RADIUS servers in the untrusted domain.
To configure NPS as a RADIUS proxy, you must create a connection request policy that contains all of the information required for NPS to evaluate which messages to forward and where to send the messages.
When you configure a remote RADIUS server group in NPS and you configure a connection request policy with the group, you are designating the location where NPS is to forward connection requests.
http://technet.microsoft.com/en-us/library/cc754518.aspx
QUESTION 15
Hotspot Question
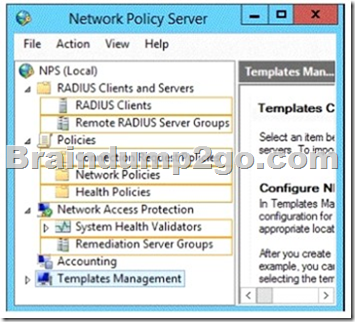
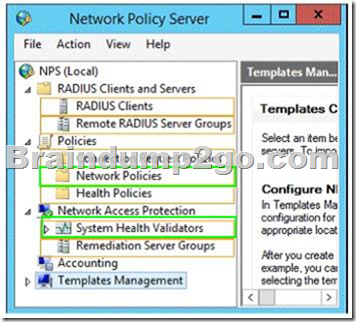
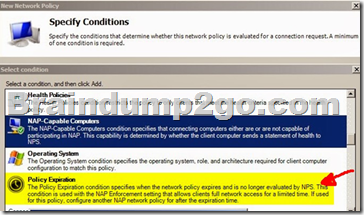
You have a server named Server1 that runs Windows Server 2012 R2.
You configure Network Access Protection (NAP) on Server1.
Your company implements a new security policy stating that all client computers must have the latest updates installed. The company informs all employees that they have two weeks to update their computer accordingly.
You need to ensure that if the client computers have automatic updating disabled, they are provided with full access to the network until a specific date and time.
Which two nodes should you configure?
To answer, select the appropriate two nodes in the answer area.
Answer:
Explanation:
QUESTION 16
Your network contains an Active Directory forest. The forest contains two domains named contoso.com and fabrikam.com. All of the DNS servers in both of the domains run Windows Server 2012 R2.
The network contains two servers named Server1 and Server2. Server1 hosts an Active Directory-integrated zone for contoso.com. Server2 hosts an Active Directory-integrated zone for fabrikam.com. Server1 and Server2 connect to each other by using a WAN link.
Client computers that connect to Server1 for name resolution cannot resolve names in fabrikam.com.
You need to configure Server1 to support the resolution of names in fabrikam.com.
The solution must ensure that users in contoso.com can resolve names in fabrikam.com if the WAN link fails.
What should you do on Server1?
A. Add a forwarder.
B. Create a stub zone.
C. Create a conditional forwarder.
D. Create a secondary zone.
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/cc771898.aspx
When a zone that this DNS server hosts is a secondary zone, this DNS server is a secondary source for information about this zone. The zone at this server must be obtained from another remote DNS server computer that also hosts the zone With secondary, you have ability to resolve records from the other domain even if its DNS servers are temporarily unavailable
While secondary zones contain copies of all the resource records in the corresponding zone on the master name server, stub zones contain only three kinds of resource records:
A copy of the SOA record for the zone.
Copies of NS records for all name servers authoritative for the zone. Copies of A records for all name servers authoritative for the zone.
http://www.windowsnetworking.com/articles-tutorials/windows-2003/DNS_Stub_Zones.html http://technet.microsoft.com/en-us/library/cc771898.aspx http://redmondmag.com/Articles/2004/01/01/The-Long-and-Short-of-Stub-Zones.aspx?Page=2
!!!RECOMMEND!!!
1.|2016/09 Latest 70-411 Exam Dumps (PDF & VCE) 445Q&As Download:
http://www.braindump2go.com/70-411.html
2.|2016/09 Latest 70-411 Exam Questions & Answers:
https://drive.google.com/folderview?id=0B75b5xYLjSSNfnNyWDFTYllvTTkteG0waVJYSFdoaDVWZTBSamh6Q0xiaUJmNEk5cUJSbFU&usp=sharing